Transient-Fault Resilience of a Capability-enabled Processor Plattform
- Typ der Arbeit: Masterarbeit
- Status der Arbeit: abgeschlossen
- Projekte: CLASSY-FI
- Betreuer: Christian Dietrich, Daniel Lohmann
- Bearbeiter: Malte Bargholz
- Ende der Arbeit: 01. Nov 2020
- Ausarbeitung: [PDF]
Fault injection is a common approach to systematically assess the resilience of a system and the effectiveness of software-based counter measures. It tries to mimic either physical causes for single event upsets (by exposing the system to e.g. heat or radiation) or their effects (by changing logic signals). For the fault injection, we use the simulation-based fault injection framework FAIL*, which extracts program traces and simulates the representative faults.
CHERI (Capability Hardware Enhanced RISC Instructions) extends conventional hardware Instruction-Set Architectures (ISAs) with new architectural features to enable fine-grained memory protection and highly scalable software compartmentalization. Its memory-protection features allow historically memory-unsafe programming languages such as C and C++ to be adapted to provide strong, compatible, and efficient protection against many currently widely exploited vulnerabilities.
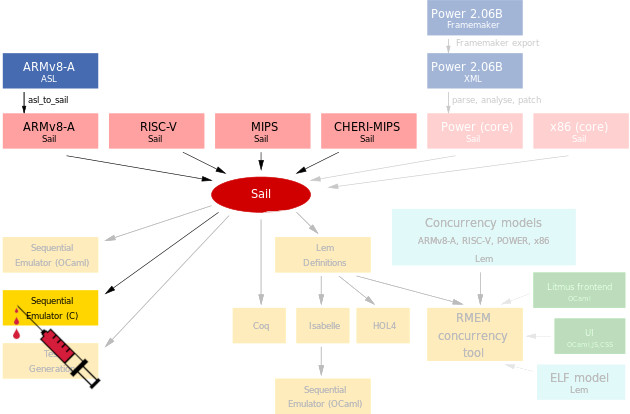
The goal of this thesis is to quantify the influence the capability-based ISA-extension CHERI has on the resilience against transient hardware faults. As a first step, you have to integrate the SAIL model for CHERI into the FAIL* fault-injection toolchain. Thereby, you can inject faults into plain MIPS and CHERI-MIPS programs.
As a second step, you will execute several fault-injection campaigns with the goal of comparing the resilience of a plain MIPS processor without CHERI extensions to different CHERI-enhanced processors. Thereby, you should answer the question if CHERI, which was designed with security in mind, is also benefitial for soft-error resilience. Different CHERI configurations, like compressed capabilities, should be considered.

